Firebird Database Converter online Help
| Prev | Return to chapter overview | Next |
Connecting to the target database
Firebird Database Converter allows you to connect to Firebird servers directly or via Secure SHell (SSH) tunnel.
| • | Direct connection |
Direct connection is the most preferable connection mode.
| • | SSH tunnel connection |
If your Firebird server does not allow direct connections from remote workstations, you can establish connection to intermediate SSH server and forward all Firebird commands through the Secure SHell (SSH) tunnel.
Irrespectively of a connection mode you should specify common credentials as follows:
Protocol
Select "Standard server" to connect to a local or remote standalone Firebird server or "Embedded server 2.5-" / "Embedded server 3.0+" to use the embedded Firebird servers that come with the software (2.5 and 3.0 accordingly).
Host
The name of machine the Firebird server and database file resides on. It is usually possible to specify TCP/IP address instead of name (like 192.168.12.34), however this functionality is not built into Firebird, instead, it is provided by underlying network layer (e.g. WinSock2), and for some implementations/configurations it can be much slower than using name. In case the server is not localhost, specify the TCP/IP port as Port number.
Login information
Since Firebird 2.1, Windows authentication has been used for configuring the server authentication mode along with the traditional login info, requiring users to log in using a user name and password defined in the security database. To use Windows authentication, check the corresponding box. Under the right conditions, this may be the most secure way to authenticate on Windows. Otherwise, set the following server security options:
User name |
The username used to connect to Firebird. User names are case insensitive on the server. |
Password |
The password for the user account on server. The server checks the user name and password against the security database. Case sensitivity is retained for the comparison. Only first 8 characters of Password are verified. |
Role |
Specify the role that the user adopts on connection to the database or leave it blank. Regardless of role memberships granted, the user has the privileges of a role at connect time only if a Role clause is specified in the connection. The user must have previously been granted membership in the role to gain the privileges of that role. |
Database name
This is either a full name of the database file (as seen from the server), or an alias defined in the server's aliases.conf file.
 More about SSH tunnel connection
More about SSH tunnel connection
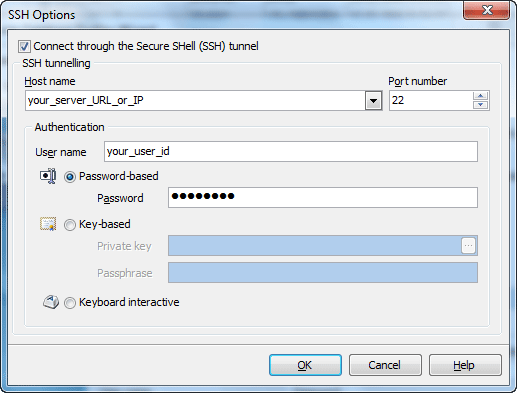
To establish connection to intermediate SSH server and forward all Firebird commands through the secure tunnel, you need to:
Host name Specify the host name or IP of your site. Note, that Firebird host name always should be set relatively to the SSH server. For example, if both of Firebird and SSH servers are located on the same computer, you should specify localhost as Host name instead of server's external host name or IP address.
Port number Enter the port number for the SSH server. 4. Enter valid User name for the remote server and select the Authentication method and set corresponding credentials.
Password-based Set the password corresponding to the specified user.
Key-based Specify the path to the Private key file with the corresponding Passphrase to log in to the remote server. Firebird Database Converter accepts keys in ssh.com or OpenSSH formats. To convert a private key from PuTTY's format to one of the formats supported by our software, use the PuTTYgen utility that can be freely downloaded from the PuTTY website.
Keyboard interactive Keyboard authentication is the advanced form of password authentication, aimed specifically at the human operator as a client. During keyboard authentication zero or more prompts (questions) is presented to the user. The user should give the answer to each prompt (question). The number and contents of the questions are virtually not limited, so certain types of automated logins are also possible. |




 Download
Download Buy
Buy